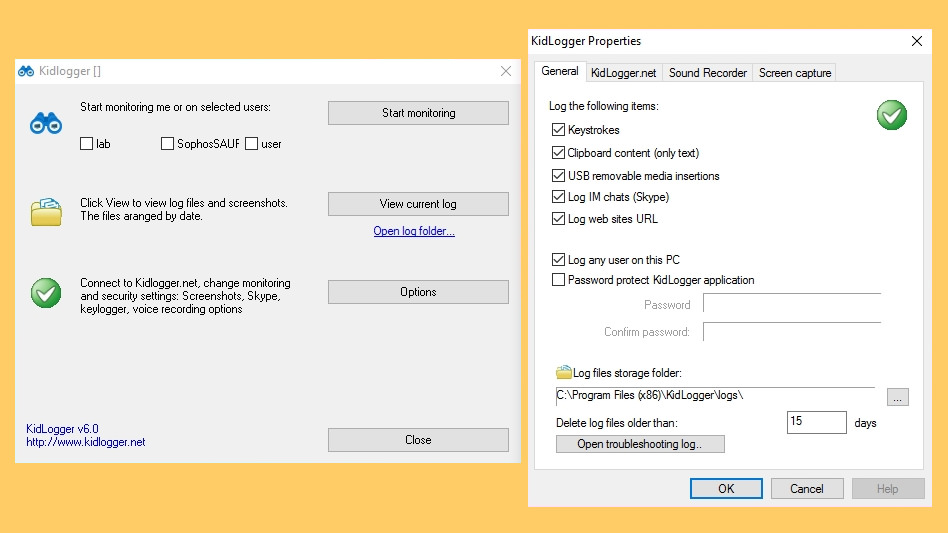
How To Monitor Internet Activity On Mac For Teens
ContentBarrier, however, is specifically designed for Mac computers and laptops, so it is much more powerful and effective at monitoring your kids’ online activity. ContentBarrier lets you block access to websites based on content by selecting categories such as gambling, sex, alcohol and racism. Jan 12, 2015 - When you are on your Mac, go to the Finder and choose Go: Network to see your child's Mac. Click on Share Screen to see the activity. Software You can purchase software to further monitor or block kids' access, which allows varying levels of censorship, depending on your kids' ages and your house rules.
Looking for some program that is REAL TIME that monitors my son's internet activity. We all use the same Apple Login and Password, so I can actually look on my Iphone and update the history every few minutes. However, I think he is deleting sites shortly after he visits them. When he deletes them quickly, they don't show up on my phone because there is a delay.
Don't want to alter his physical Ipad, would rather use something that either monitors the cloud and records activity every 5 minutes or so. Does anyone know if anything like this exists??? Thanks so much!!! Looking for some program that is REAL TIME that monitors my son's internet activity.
We all use the same Apple Login and Password, so I can actually look on my Iphone and update the history every few minutes. However, I think he is deleting sites shortly after he visits them. When he deletes them quickly, they don't show up on my phone because there is a delay. Don't want to alter his physical Ipad, would rather use something that either monitors the cloud and records activity every 5 minutes or so. Does anyone know if anything like this exists??? Thanks so much!!! Click to expand.Before I start I don't have a complete answer for you but maybe something will point you in the right direction.
Someone else may have a better solution if none of this helps. Firstly, you might look into Restrictions, settings you can restrict and configure on the device itself and put behind a passcode. As far as I know that doesn't do quite what you need though.
It sounds like you may be looking for an MDM (Mobile Device Management) solution. These are products or services that allow you to lock down or monitor iOS devices. More usually they are used in a corporate setting so companies can lock down and monitor their devices and they can be complicated to use. I'm not sure if there's something that's more geared to the personal or family user (though if there isn't it seems like a gap in the market).I had a quick google and something called Spiceworks came up but I've never tried it and didn't look deeply into it. Maybe this will help point you in the right direction (though maybe not) In before someone comes in and gives you a lecture on trusting your children.
Yes but not user friendly, the name of the program is called Wireshark. As for something more user friendly, the OS itself might have some built in tools to provide this information, macOS can limit by outright blocking connections, Windows has a parenting feature that they keep reducing which may not produce the desired effect. I'm going to start off listing what you should know and what it doesn't do so you can skip what it does if I lose you.
What you need. A network card that can work in monitor mode. General knowledge of IP addresses and IP packet structure. Using regular expressions to filter your results is a plus but not required. An Ethernet (not wireless) connection to the end most device before the modem.
(most often this is a router) Alternatively you can turn your computer into the Access Point and route all wireless traffic to your computer and send it through the Ethernet connection What it doesn't do. It does not grab login information from encrypted websites (https websites) It does not provide an easy to read chart when you are ready to review. It does not work without a network card that can be run in promiscuous (monitor) mode.
What it does do. It can grab snapchat images sent to and from a device on your network. It can grab login credentials from unsecure websites accessed from your network.
It can grab images sent to and from your network. It can grab unsecure text messages sent over data connections. It can grab voip phone calls.
It can provide a list of websites that your son has accessed since you started monitoring. It can provide forum posts on an unsecured forum such as this one. It can provide access times to the nearest millisecond on when a website was accessed. My child thought I was lying, I proved her wrong when I showed her a message that she would never have let me see until she was 25 and over it. This also monitors all of the devices on your network but you can filter it down to just your kid's devices. Yes but not user friendly, the name of the program is called Wireshark. As for something more user friendly, the OS itself might have some built in tools to provide this information, macOS can limit by outright blocking connections, Windows has a parenting feature that they keep reducing which may not produce the desired effect.
I'm going to start off listing what you should know and what it doesn't do so you can skip what it does if I lose you. What you need. A network card that can work in monitor mode. General knowledge of IP addresses and IP packet structure. Using regular expressions to filter your results is a plus but not required.
An Ethernet (not wireless) connection to the end most device before the modem. (most often this is a router) Alternatively you can turn your computer into the Access Point and route all wireless traffic to your computer and send it through the Ethernet connection What it doesn't do. It does not grab login information from encrypted websites (https websites) It does not provide an easy to read chart when you are ready to review. It does not work without a network card that can be run in promiscuous (monitor) mode.
What it does do. It can grab snapchat images sent to and from a device on your network. It can grab login credentials from unsecure websites accessed from your network.
It can grab images sent to and from your network. It can grab unsecure text messages sent over data connections. It can grab voip phone calls. It can provide a list of websites that your son has accessed since you started monitoring. It can provide forum posts on an unsecured forum such as this one.
It can provide access times to the nearest millisecond on when a website was accessed. My child thought I was lying, I proved her wrong when I showed her a message that she would never have let me see until she was 25 and over it. This also monitors all of the devices on your network but you can filter it down to just your kid's devices.
Download java 1.8 jdk for mac. I don't know what I'm going to do when I have kids. My parents were pretty overprotective about a lot of things, but not so when it came to the Internet. I was a teen in the 90s and early 2000s, and my parents were (still are) clueless when it comes to computers, so other than putting the computer in a 'public' place (which they didn't) they wouldn't have known how to monitor my internet use even if they wanted to. They didn't even know what a browser history was! Yes, I visited sites that were not intended for minors, but I was a teenaged boy! If I have my own kids one day, I really don't know to what extent I should monitor or censor what they're exposed to. I grew up without such censorship and I'm a fine upstanding citizen, if I do say so myself.
I don't know what I'm going to do when I have kids. My parents were pretty overprotective about a lot of things, but not so when it came to the Internet.
I was a teen in the 90s and early 2000s, and my parents were (still are) clueless when it comes to computers, so other than putting the computer in a 'public' place (which they didn't) they wouldn't have known how to monitor my internet use even if they wanted to. They didn't even know what a browser history was! Yes, I visited sites that were not intended for minors, but I was a teenaged boy! If I have my own kids one day, I really don't know to what extent I should monitor or censor what they're exposed to. I grew up without such censorship and I'm a fine upstanding citizen, if I do say so myself.
You can set your router to log websites. If your router doesn't do it out of the box, get one that does.
Software solutions, in my opinion, are very easy to circumvent. I also believe that monitoring or censoring the internet is an exercise in futility, but could have good unintended consequences: My parents never restricted my internet, and allowed me to have a computer in my room. I grew up in the 90s and early 2000s.
This is despite the fact that my father is a software and hardware engineer, knows quite a lot about technology, and at that age tough me everything I know. Finding whatever I wanted online was no problem for me. My best friend's parents though were crazy about it though. We liked going to steak and cheese dot com, which was blocked for obvious reasons. Initially they installed a little snooping and lockout program on his desktop in his room (initially Windows 98SE, later Windows 2000). After telling his parents we were doing research for school, so they unlocked his browsing, we proceeded to find instructions online on how to disable this snooping program without letting the administrator know that something was up.
Later, they installed a different program. Again, we manually found keys in the Windows registry that let us disable certain functionalities. Later, his parents installed a network-based censoring program that was configured to block his computer. We learned how to spoof a computer's MAC address.
They upped the security restrictions to include all computers but their own, we learned how to kick their computers off the network and spoof their MAC address. They upped the security restrictions to apply to all computers all the time, we found a program that brute-forced the admin password for the router.
They got a different router. And we went to college. Both of us went into some form of engineering, armed with the large amount of Windows registry and IP networking experience we learned fighting his parents. Moral of the story, locking your network might encourage your kids to learn to hack. You can set your router to log websites. If your router doesn't do it out of the box, get one that does.
Software solutions, in my opinion, are very easy to circumvent. I also believe that monitoring or censoring the internet is an exercise in futility, but could have good unintended consequences: My parents never restricted my internet, and allowed me to have a computer in my room. I grew up in the 90s and early 2000s. This is despite the fact that my father is a software and hardware engineer, knows quite a lot about technology, and at that age tough me everything I know. Finding whatever I wanted online was no problem for me. My best friend's parents though were crazy about it though.
We liked going to steak and cheese dot com, which was blocked for obvious reasons. Initially they installed a little snooping and lockout program on his desktop in his room (initially Windows 98SE, later Windows 2000). After telling his parents we were doing research for school, so they unlocked his browsing, we proceeded to find instructions online on how to disable this snooping program without letting the administrator know that something was up. Later, they installed a different program.
Again, we manually found keys in the Windows registry that let us disable certain functionalities. Later, his parents installed a network-based censoring program that was configured to block his computer. We learned how to spoof a computer's MAC address. They upped the security restrictions to include all computers but their own, we learned how to kick their computers off the network and spoof their MAC address.
They upped the security restrictions to apply to all computers all the time, we found a program that brute-forced the admin password for the router. They got a different router.
And we went to college. Both of us went into some form of engineering, armed with the large amount of Windows registry and IP networking experience we learned fighting his parents. Moral of the story, locking your network might encourage your kids to learn to hack. Click to expand.This guy is obviously not sophisticated enough to find a commercial solution, let alone implement WGP or iOS MDM on his own.
Further, both of those will alert the administrator when there has been tampering and the administrator can take certain actions to protect data, but both are very easy to circumvent in terms of actually using the client machine. On a PC, WGP will not prevent me from booting a Linux distro from a USB drive. On iOS, the owner of the device can easily delete the MDM profile. Both are not the solution the OP is looking for.
Add or remove columns in each of these panes by choosing View Columns from the menu bar. The View menu also allows you to choose which processes are shown in each pane:.
All Processes. All Processes Hierarchically: Processes that belong to other processes, so you can see the parent/child relationship between them.
My Processes: Processes owned by your macOS user account. System Processes: Processes owned by macOS. Other User Processes: Processes that aren’t owned by the or current user. Active Processes: Running processes that aren’t sleeping. Inactive Processes: Running processes that are sleeping. Windowed Processes: Processes that can create a window. These are usually apps.
Selected Processes: Processes that you selected in the Activity Monitor window. Applications in the last 8 hours: Apps that were running processes in the last 8 hours. The CPU pane shows how processes are affecting CPU (processor) activity: Click the top of the “% CPU” column to sort by the percentage of CPU capability used by each process.
This information and the information in the can help identify. More information is available at the bottom of the CPU pane:. System: The percentage of CPU capability currently used by system processes, which are processes that belong to macOS. User: The percentage of CPU capability currently used by apps that you opened, or by the processes those apps opened. Idle: The percentage of CPU capability not being used. CPU Load: The percentage of CPU capability currently used by all System and User processes. The graph moves from right to left and updates at the intervals set in View Update Frequency.
The color blue shows the percentage of total CPU capability currently used by user processes. The color red shows the percentage of total CPU capability currently used by system processes. Threads: The total number of threads used by all processes combined.
Processes: The total number of processes currently running. You can also see CPU or GPU usage in a separate window or in the Dock:. To open a window showing current processor activity, choose Window CPU Usage. To show a graph of this information in your Dock, choose View Dock Icon Show CPU Usage. To open a window showing recent processor activity, choose Window CPU History. To show a graph of this information in your Dock, choose View Dock Icon Show CPU History.
To open a window showing recent graphics processor (GPU) activity, choose Window GPU History. Energy usage related to such activity is incorporated into the energy-impact measurements in the tab of Activity Monitor.
The Memory pane shows information about how memory is being used: More information is available at the bottom of the Memory pane:. Memory Pressure: The Memory Pressure graph helps illustrate the availability of memory resources. The graph moves from right to left and updates at the intervals set in View Update Frequency. The current state of memory resources is indicated by the color at the right side of the graph:. Green: Memory resources are available. Yellow: Memory resources are still available but are being tasked by memory-management processes, such as compression.
Red: Memory resources are depleted, and macOS is using your startup drive for memory. To make more RAM available, you can quit one or more apps or install more RAM. This is the most important indicator that your Mac may need more RAM. Physical Memory: The amount of RAM installed in your Mac. Memory Used: The total amount of memory currently used by all apps and macOS processes.
App Memory: The total amount of memory currently used by apps and their processes. Wired Memory: Memory that can’t be compressed or paged out to your startup drive, so it must stay in RAM.
The wired memory used by a process can’t be borrowed by other processes. The amount of wired memory used by an app is determined by the app's programmer. Compressed: The amount of memory in RAM that is compressed to make more RAM memory available to other processes. Look in the Compressed Mem column to see the amount of memory compressed for each process. Swap Used: The space used on your startup drive by macOS memory management. It's normal to see some activity here.
As long as memory pressure is not in the red state, macOS has memory resources available. Cached Files: Memory that was recently used by apps and is now available for use by other apps. For example, if you've been using Mail and then quit Mail, the RAM that Mail was using becomes part of the memory used by cached files, which then becomes available to other apps. If you open Mail again before its cached-files memory is used (overwritten) by another app, Mail opens more quickly because that memory is quickly converted back to app memory without having to load its contents from your startup drive.
For more information about memory management, refer to the. The Energy pane shows overall energy use and the energy used by each app:. Energy Impact: A relative measure of the current energy consumption of the app.
Lower numbers are better. A triangle to the left of an app's name means that the app consists of multiple processes. Click the triangle to see details about each process. Avg Energy Impact: The average energy impact for the past 8 hours or since the Mac started up, whichever is shorter. Average energy impact is also shown for apps that were running during that time, but have since been quit. The names of those apps are dimmed. App Nap: Apps that support App Nap consume very little energy when they are open but not being used.
For example, an app might nap when it's hidden behind other windows, or when it's open in a space that you aren't currently viewing. Preventing Sleep: Indicates whether the app is preventing your Mac from going to sleep. More information is available at the bottom of the Energy pane:. Energy Impact: A relative measure of the total energy used by all apps. The graph moves from right to left and updates at the intervals set in View Update Frequency. Graphics Card: The type of graphics card currently used.
 Mac OS® X; System Software. Do not operate, power off, or disconnect the Blu-ray Disc player from the AC power outlet until after the update is complete.
Mac OS® X; System Software. Do not operate, power off, or disconnect the Blu-ray Disc player from the AC power outlet until after the update is complete.
Higher–performance cards use more energy. Macs that support save power by using integrated graphics. They switch to a higher-performance graphics chip only when an app needs it. 'Integrated' means the Mac is currently using integrated graphics. Means the Mac is currently using high-performance graphics. To identify apps that are using high-performance graphics, look for apps that show 'Yes' in the Requires High Perf GPU column. Remaining Charge: The percentage of charge remaining on the battery of a portable Mac. Time Until Full: The amount of time your portable Mac must be plugged into an AC power outlet to become fully charged.
Time on AC: The time elapsed since your portable Mac was plugged into an AC power outlet. Time Remaining: The estimated amount of battery time remaining on your portable Mac.
Time on Battery: The time elapsed since your portable Mac was unplugged from AC power. Battery (Last 12 hours): The battery charge level of your portable Mac over the last 12 hours. The color green shows times when the Mac was getting power from a power adapter. As energy use increases, the length of time that a Mac can operate on battery power decreases. If the battery life of your portable Mac is shorter than usual, you can use the Avg Energy Impact column to find apps that have been using the most energy recently.
Quit those apps if you don't need them, or contact the developer of the app if you notice that the app's energy use remains high even when the app doesn't appear to be doing anything. The Disk pane shows the amount of data that each process has read from your disk and written to your disk. It also shows 'reads in' and 'writes out' (IO), which is the number of times that your Mac accesses the disk to read and write data. The information at the bottom of the Disk pane shows total disk activity across all processes. The graph moves from right to left and updates at the intervals set in View Update Frequency. The graph also includes a pop-up menu to switch between showing IO or data as a unit of measurement. The color blue shows either the number of reads per second or the amount of data read per second. The color red shows either the number of writes out per second or the amount of data written per second.
To show a graph of disk activity in your Dock, choose View Dock Icon Show Disk Activity. The Network pane shows how much data your Mac is sending or receiving over your network. Use this information to identify which processes are sending or receiving the most data. The information at the bottom of the Network pane shows total network activity across all apps.
The graph moves from right to left and updates at the intervals set in View Update Frequency. The graph also includes a pop-up menu to switch between showing packets or data as a unit of measurement.
The color blue shows either the number of packets received per second or the amount of data received per second. The color red shows either the number of packets sent per second or the amount of data sent per second. To show a graph of network usage in your Dock, choose View Dock Icon Show Network Usage. In macOS High Sierra 10.13.4 or later, Activity Monitor shows the Cache pane when is enabled in the Sharing pane of System Preferences.
The Cache pane shows how much cached content that local networked devices have uploaded, downloaded, or dropped over time. Use the Maximum Cache Pressure information to learn whether to adjust Content Caching settings to provide more disk space to the cache. Lower cache pressure is better. The graph at the bottom shows total caching activity over time. Choose from the pop-up menu above the graph to change the interval: last hour, 24 hours, 7 days, or 30 days.